Business Email Compromise and the Risk to Your Organisation
One of the most common ways cybercriminals are now targeting SMEs in Australia is with a technique known as Business Email Compromise, or BEC for short. If you’ve never heard of this, you are already behind the curve and potentially putting your business at risk.
What is BEC?
BEC is a type of cybercrime targeted at businesses or organisations, with the aim of either causing financial or reputational damage. BEC attacks, or Email Account Compromise (EAC), occur when a business email (real or spoofed) is used to compromise a business. Attackers will use email accounts to deceive employees and trick them into handing over confidential company information or money.
IS BEC a risk to your business?
The short and definitive answer to this question is YES.
BEC is one of the most financially damaging cyber attacks facing businesses of all sizes all over Australia. It is a common misconception that BEC is predominantly an issue for large organisations, but this is far from the reality. Small to Medium Enterprises (SMEs) are just as prone to being a target, especially if they do not have the proper protections.
Here are some key statistics from the Australian Cyber Security Centre (ACSC) report surrounding the average loss for small, medium and large enterprises in Australia for the 2021-2022 financial year.
How do BEC scams work?
What Types of BEC Scams are There to Look Out For?
BEC captures five different styles of scams. Here are the types of scams, the target employee type and
what is motivating the attack.
Data Theft
Target Employee
BEC captures five different styles of scams. Here are the types of scams, the target employee type and what is motivating the attack.
Goal of Attacker
To gain access to sensitive or confidential company information about certain employees, partners or key stakeholders within a business.
Signs to look out for
- Urgent request for information
- Spoofed email domains with misspellings
- New correspondence from new employee
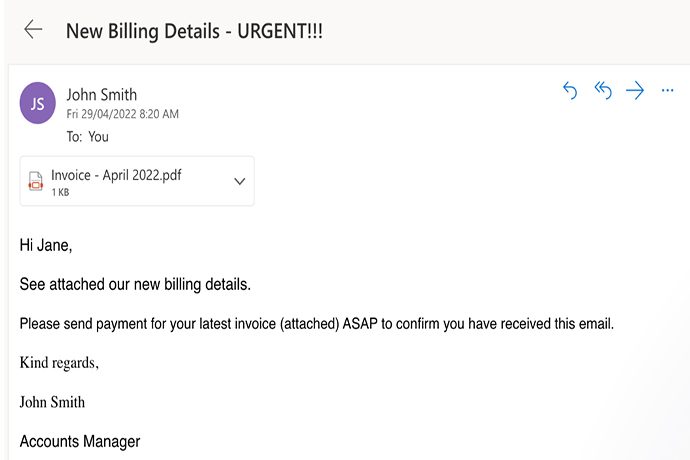
False Invoice Scheme
Target Employee
A scammer will pose as a vendor that works with the business and send an email with a fake invoice to an identified or random employee within the business.
Goal of Attacker
To gain money from a business thinking they are paying a legitimate vendor or supplier.
Signs to look out for
- Different bank account listed on invoice than usual vendor
- Direct requests to a new bank account due to problems with an old account
CEO Fraud
Target Employee
An attacker may compromise a legitimate CEO’s email account or use a fake domain to impersonate a CEO of a company to target employees.
Goal of Attacker
To prompt employees to make certain purchases, make a money transfer or buy gift cards with company money.
Signs to look out for
- Email domains are misspelt
- Urgency behind requests
- Email content does not match usual tone of CEO
- Asks for photos of serial numbers of previously purchased gift cards
Account Compromise
Target Employee
Can include a combination of malicious cyber tactics including phishing and malware to gain access to an employee with financial responsibility.
Goal of Attacker
To compromise an employee’s legitimate business email to send invoices to outside vendors and request money to a fraudulent bank account.
Signs to look out for
- Unrecognised sent or deleted emails
- Mismatch of bank details on invoices
Lawyer Impersonation
Target Employee
This attack initially targets lawyers to penetrate a business on the law firm’s client list.
Goal of Attacker
To compromise a legitimate law firm’s email account to access their client list and request billed hours to be paid to a fraudulent bank account.
Signs to look out for
- Out of the blue request for lawyers fees
- Different bank details than previous transfer
- Unusual tone in email or a sense of urgency for payment
Many of the above scams have similar attack features but are usually delivered searching for a different goal of compromise. These may include more BEC scams as cyber-attacks and criminals become more sophisticated.
How do you defend against BEC Attacks?
The best line of defence starts with ensuring all employees, from top to bottom, understand the kind of risks that are out there. On top of this, it’s essential to have a range of tight-knit security controls and policies in place to mitigate incoming threats.
Here are some tips to secure your business against BEC attacks.
- Secure your domain by ditching free web-based emails for a company domain.
- Add layers of security for email accounts through Multi-Factor Authentication (MFA).
- Be cautious of unknown emails, links, and attachments.
- Guard your domain by registering variations of your business name to protect against spoofing.
- Always verify every sender’s address for irregularities.
- Forward emails where possible, including relevant cc’d parties
- Limit oversharing on social media and websites
- Verify transfers before sending with trusted contacts
- Watch for abrupt changes in customer or vendor habits
- Keep up to date with scam types and trending cyber attack vectors
Conclusion
As technology and cyber criminals evolve, businesses must adapt to the ever-changing cyber threat landscape. Fostering a cyber-secure and conscious culture is critical in shielding your SME from cybercriminals. Pair this with a concrete incident response plan to help build impenetrable businesses.
Being cyber resilient means taking pre-emptive steps, even when it seems those around you aren’t.
In essence, the emphasis on cyber resilience underscores the nation’s commitment to ensuring business continuity and protecting its citizens’ digital assets and information. The digital future is bright only if we do our due diligence. Want to make your company cyber-resilient? Talk to our experts at LEAP Strategies and pave your way toward a cyber-resilient future!




